Internet Of Things (IoT) is a vision where every single element that exists in the world has the potential to connect to the internet. It is the most vital to digital transformation and drives immense economic opportunities for various industries. It enables superb innovations that reach almost all sectors starting from childcare, eldercare, transportation, education, hospitality, mining, etc.
The IoT technology is growing amazingly fast. As per investigations, it is noted that by the end of 2025, the whole world will have nearly 41.7 billion connected devices generating overall 79.4 zettabytes of data. So, from the huge number, we can predict how important it is to secure the data.
IT vs. OT
To understand IoT security, it is very much necessary to understand first the difference between IT and OT.
- Information Technology (IT): In an organization, IT networks to deal with the flow of information or data or information.
- Operational Technology (OT): OT networks handle the operation as well as control of physical processes along with machinery.
There are so many discussions going on regarding the integration of IT and OT. Many think that filling the gap between these two is vital, whereas some believe that they should remain separate.
According to pundits and analysts, when considering IoT cybersecurity, it is important to find a dedicated way to transfer data between IT and OT networks while segregating access and control to OT networks to manage safe control of the technology.
What is the security concern with IoT?
Although it feels like IoT devices are too specialized or small to be dangerous, there is actual risk involved in this as they are network-connected. Even very small devices connected to the internet can be dangerous. Once an attacker has owned control over the device, they can easily steal information, interrupt the service delivery, or perform any other cybercrime they would do with a system. If the cyber attacks are compromised in any way, it not only affects unreliable operations and data breaches but also harms other facilities or worse to the human beings operating those facilities.
What else should be considered with IoT service security?
IoT Security is also driven by:
- Fragmentation or Device heterogeneity
Several organizations utilize various devices using different chips, running numerous software, and utilize different techniques to connect. This process is called device heterogeneity. It generates a challenge to control as well as update all your connected devices but there are different software solutions to ease the process
- Connection to important operational technology
Most of the businesses would like to take advantage of the connections, but can’t compromise with the revenue loss, in case services are attacked even for a few days. The good thing is that there are trustworthy IOT security organizations that provide software solutions to protect your IoT services.
- Challenges with the security of legacy devices
Some devices are there before IOT comes into the picture. These existing devices have never been “hardened”, the process to find out and reduce vulnerabilities. So many legacy devices are cost-effective or not built with particular IoT security in mind.
How do IoT attacks happen?
Since the IoT connectivity covers a huge area and most of the time unknown attacks surface as well as IoT devices and apps dedicated to certain services can hold large accretion of operational, personal, and corporate data, security pros have to go beyond the usual information security needs of reliability, privacy, and accessibility.
Security pros are concerned with cyberattacks and data breaches. However, since an IOT vulnerability can create a life-threatening shutdown or danger of revenue-generated operations, they must concern themselves with safe & secure connectivity, threat monitoring, device hardening, and security posture management, and most importantly securing information on the cloud backend.
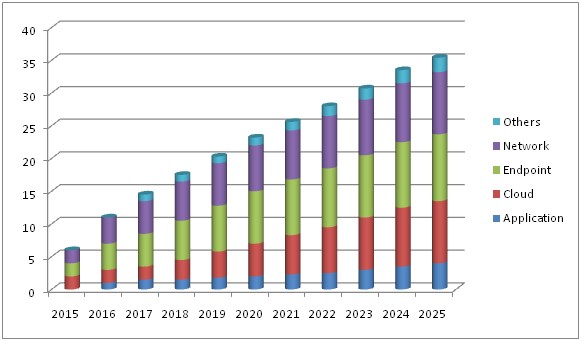
IOT security market size in between 2015-2025
What steps should be taken to secure IoT services?
The ultimate IoT security is based on cloud security. The architecture of the cloud is designed in such a way that it provides inherent security provisions as well as best practices to craft a solid base for effortless but powerful IoT protection. You can follow these best practices to secure your IoT services in the cloud
- Understand your shared responsibility: Know your roles & responsibility along with your partners to maintain the security of your IoT services. These must be documented upfront, and you must strive to examine and pick trustworthy partners as well as vendors with security practices that go well with the prime objectives of your business.
- Implement a strong identity foundation: Utilize the least opportunity protocol and involve duties segregation with proper authorization for each and every communication. Integrate opportunity management and decrease or even eradicate dependency upon long-term credentials.
- Enable traceability: Scrutinize, cautious, and monitor activities and changes to your real-time environment. Include logs as well as metrics with IoT service systems to respond automatically and take action.
- Apply security at all layers: Instead of concentrating on providing protection to a single outer layer, use a defense-in-depth technique along with other security controls. Use it in all layers (for example, virtual private cloud (VPC), edge network, load balancer, subnet, operating system, every instance, and application).
- Automate security best practices: Software-based automatic security mechanisms are there to improvise your expertise to scale safely, cost-effectively, and quickly. Build safe architectures including control applications that are handled as well as defined as code in different version-controlled templates.
- Protect data in travel and at rest: Segregate your information into different sensitivity levels and use different mechanisms like tokenization, encryption, and access control.
- Keep people away from data: To eliminate or decrease the requirement of manual processing or direct accessing of data, craft mechanisms as well as suitable tools. This limits the risk of modification, loss, and other human-made errors when managing sensitive data.
- Prepare for security events: Build a process to manage incidents that align with the actual needs of your firm. To improve your detection speed, study, and recovery, run incident response simulations as well as use automatic tools.
Final Thoughts
From all these discussions, it is clear that IOT service security has great importance as at every stage we push the boundaries of IOT and the data we extract from the technology. This data is very powerful, and the ease with which we are able to interact and extract it makes for an alluring proposition.
With all the benefits of IoT, we need to be very cautious about how all the services can be done safely & securely. While discussing the security and convenience of IoT, there are so many solutions that are amazing in their simplicity and many of these can help you to tackle the IOT security idea from dream to reality.

