Security is more crucial than ever!!!
Every organization should confront a few major security concerns such as
⦁ Safety
⦁ Security and
⦁ Protection of information
If you’re looking for the best security tool to protect your business, look no further than SIEM – Security Information and Event Management.
Let’s have a look at what SIEM is, features, working model, benefits and a lot more.
What is SIEM?
Security Information and Event Management is a collection of tools or services that offers a holistic view of companies information security. Keeping it simple, SIEM provides companies with next-generation analytics and response.
SIEM software connect
⦁ Security Information Management
⦁ Security Event Management
As mentioned earlier, SIEM will provide security information and alerts in real-time. The software coordinates events against organization rules. With security alerts, the IT team can become proactive. They can fight against unauthorized access and security threats.
Why Security Information and Event Management?
Whether you’re running a small business or a large enterprise, SIEM software is important for you. With SIEM, it’s easier to manage security.
SIEM software helps IT teams by offering insights and log activities performed within the IT infrastructure. Also, provides detailed reporting, log management, data analysis and more.
With powerful security information and event management, companies can:
⦁ Eliminate the hidden spots by collecting complete security and event data into one location.
⦁ Identify suspicious activities without hassles.
⦁ Get a holistic view that allows the IT team to monitor round the clock and enforce according to company policies.
Features of SIEM
Artificial intelligence
⦁ Normalization
⦁ Unlimited log collection
⦁ Instant reports and alerts
⦁ Advanced investigation and behaviour analysis
⦁ Integration with security controls
⦁ Compliance reporting
⦁ Forensics capabilities
⦁ Advanced early threat detection
⦁ Effective data protection
How does SIEM work?
Security information and event management is not a new technology. This software has been helping companies for the past two decades. And over time, SEM has become an important software for SOC – Security Operations Center. The tool provides around the clock monitoring, log event information and instant alerts.
SIEM tool helps IT and security teams purely concentrate on identifying and responding to the security issues or threats that really matter. By using a predefined set of rules and regulations, companies can set alerts according to the priority (low, medium or high).
Let’s consider, an employee can attempt 30 failed logins in just 30 minutes. This activity could be set as a low priority. Because employees may forget their login credentials.
However, an employee can attempt 30 failed login in 5 minutes could be set as a high-priority event.
Security information and event management software can easily detect and sort the information into multiple categories. It includes failed logins, malicious attacks, etc.
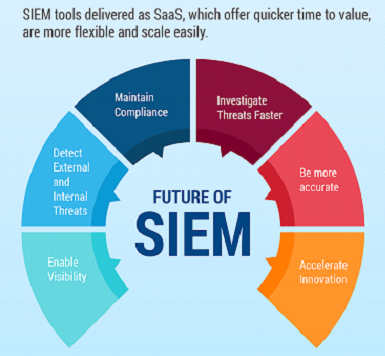
Advantages of SIEM
Hope you got a clear picture of security information and event management.
Now let’s have a look at the advantages of using SIEM software.
SIEM provides a holistic view of companies’ information security infrastructure. The tool will make it easier to collect and analyse the security data. Ultimately, keep the organization safe and secure.
Identifies events according to the data input. The software will pull the security information from multiple sources and easily correlate depending on the activity within the individual source.
The tools work effectively for the organization who are revolving around event logs, security programs, help desk, audit, network troubleshooting and more.
SIEM offers scalability. It means SIEM supports a massive amount of security information. So, companies can constantly increase their information with no effort.
The software provides instant security alerts, warnings, threat notification and detection. Also, the tool provides an automatic response with respect to the integrations.
SIEM is useful for security analysis, compliance and more. It’s no surprise that the requirement of compliance regulation is plenty, therefore organizations should invest in the right SIEM tool.
SIEM tools
There are thousands of SIEM solutions available on the market. Let’s have a look at the most popular SIEM tools.
Solar Winds Security Event Manager
Want to improve security posture? Yes! Look no further than SolarWinds.
The platform offers comprehensive log management features ranging from compliance reporting to advanced analytics. The feature “File Integrity Checker” is used to track the changes that are made to the file. On the other hand, SolarWinds allow companies to customize and enhance security measures with data encryption techniques, USBs, smart card integrations and more.
Splunk
Splunk is the leading SIEM software in the market. Over a decade, companies have been using Splunk for security concerns.
Splunk allows companies to analyze, investigate, monitor and act with any structure, any source, any insight and any timescale.
The Splunk solution offers real-time threat monitoring using visual correlations. Also, rapid investigations can easily trace out the dynamic activities that are linked with security threats.
LogRhythm
LogRhythm is one of the popular SIEM solutions. The tool helps companies tell a cohesive story around the users and host information. Also, making it simple to gain advanced insights that are required to remediate security events faster.
LogRhythm is a powerful solution for critical log events on Windows. Installing and configuring LogRhythm software is simple, with no hassles involved. With a user-friendly dashboard, IT staff can simplify their workflow.
The platform offers real-time event visibility around your IT environment. This way, you can quickly analyse, identify and prioritize the issue. LogRhythm software has the ability to map security and overall IT operations to the already existing framework.
Capabilities of SIEM
Let’s have a look at the capabilities of security information and event management tool:
Log management
Log management is the fundamental requirement for a powerful SIEM tool. Log management is responsible for collecting and storing the log files from several sources in a centralized location. This way, the IT team can easily access the secure data with a single click.
When the log information arrives at the SIEM tool in real-time, it helps to normalize the log data for accurate analysis. However, normalization of the information is a must because multiple devices from multiple vendors have unique log data formats. Let’s consider, the log data format of vendor X’s firewall will be different from vendor Y’s firewall.
Security event correlation
While considering SIEM capabilities, security event correlation plays a vital role. With a log management feature, SIEM will analyze accumulated information for potential signs of threat infiltration.
Consider, the employee failed login could be considered as nothing. But an employee failing to log in on several applications around the IT environment is the indicator of the potential digital threat.
Security alerts
Your SIEM software must be administered and keep your entire IT security team up to date with the potential threats. The security alerts could be from dashboard notifications, email or text message alerts.
The security alerts by the SIEM solution will enable your IT team to quickly identify the attacks. The real time security notifications can decrease the time period of the threat person is within your organization. This way, security alerts will prevent you from losing money or damaging your organization’s reputation.
Machine learning
Machine learning is not a new concept for companies. This capability in the SIEM software allows detecting the threat indicators automatically. Also, adapt to new data without any information from the IT team. As a result, machine learning can save the time and effort of your IT team.
End-to-end incident management
In an organization, identifying a security event can be a single element of incident management. There are several elements such as
⦁ Identifying the security incident
⦁ Thoroughly analysis the identified event
⦁ Verifying the event
⦁ Assigning the task for a resolution to an individual or group of members
⦁ Obtaining necessary steps for mitigating the event
⦁ Implementing the necessary measures in order to prevent similar events from happening in the coming days
An outstanding SIEM tool will help your organization in handling security events. The measures are taken from identifying to mitigation. SIEM tools for next-generation can support your IT team to automate event response workflow.
User and Entity Behavior Analytics (UEBA)
UEBA is important to create a proper baseline for daily activities performed within the business infrastructure. Keep a note, the efficiency of the baseline may vary during the initial period of the SIEM tool.
After an adequate amount of information is received, it recognises the variation from baseline daily activities. Later, it flags the identified event and sends them for investigation. UEBA is the latest addition to SIEM solution capabilities. The feature is supported by predicting attacks in advance. There are few SIEM tools that contribute a risk score for every member of the network. The risk score will be determined by their activities.
Advanced report presentation
It doesn’t matter how advanced the SIEM capability is, it would be useless when your IT staff cannot gain knowledge of the warning or threat intelligence your SIEM presents. Simply put, SIEM tools are required to display the complete information of your security in a readable or easy-to-digest format. The format can be clear dashboards, graphics, bar diagrams or pie charts.

