From Blue Whale to Momo, REvil to Sodinokibi, Cyber-attacks are all over the news these days. All of us have seen the news about Cybersecurity issues happening around us. We have seen multiple instances of online threats like above mentioned that migh5t lead to situations of self-harm and the threat is not pertaining to a particular person or a firm. The issue has a widespread grasp over any institution or an individual, whether it may be a private company, a government institution, or an individual. Ransomware like REvil and Sodinokibi have caused data leaks and raised several security threats. Maintaining the confidentiality of our data has become one of the major problems of the day. However we try we find a struggle as these attacks come in new disguises everyday.
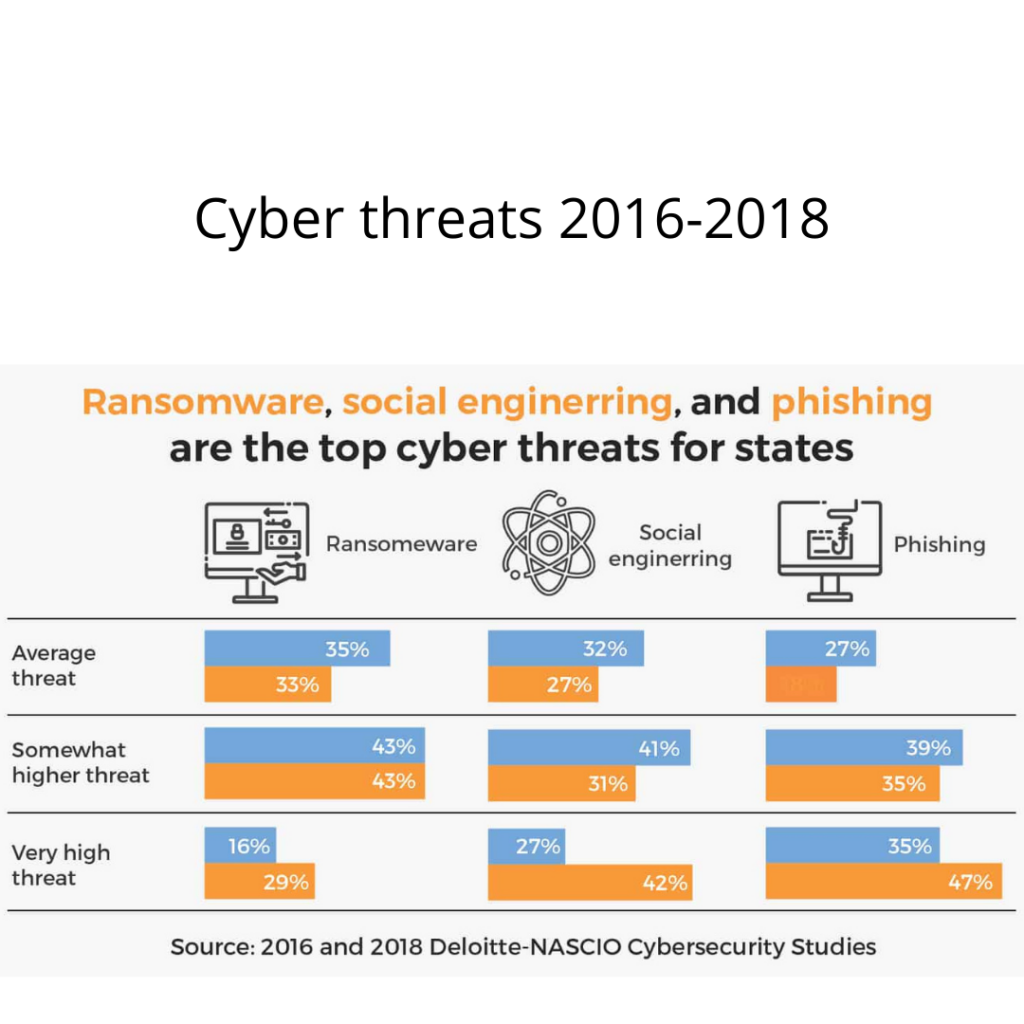
As we rely upon the internet for everything, right from entertainment to our official needs, it is of high importance to ensure our data remains safe. We have seen many instances of cybersecurity issues like ransomware, malware attacks, and phishing emails. The only way to protect ourselves from these attacks is to have a cyber-security policy or a cybersecurity setup.
Why Cyber Attacks Happen
Cyber-attacks happen in many ways. However, these attacks aim to destroy, access, or acquire control over any data that can lead to serious conflicts or vulnerabilities to an enterprise, an individual, or a state-owned firm like the defense system of the country, the confidential information about the internal matters of the country, etc.
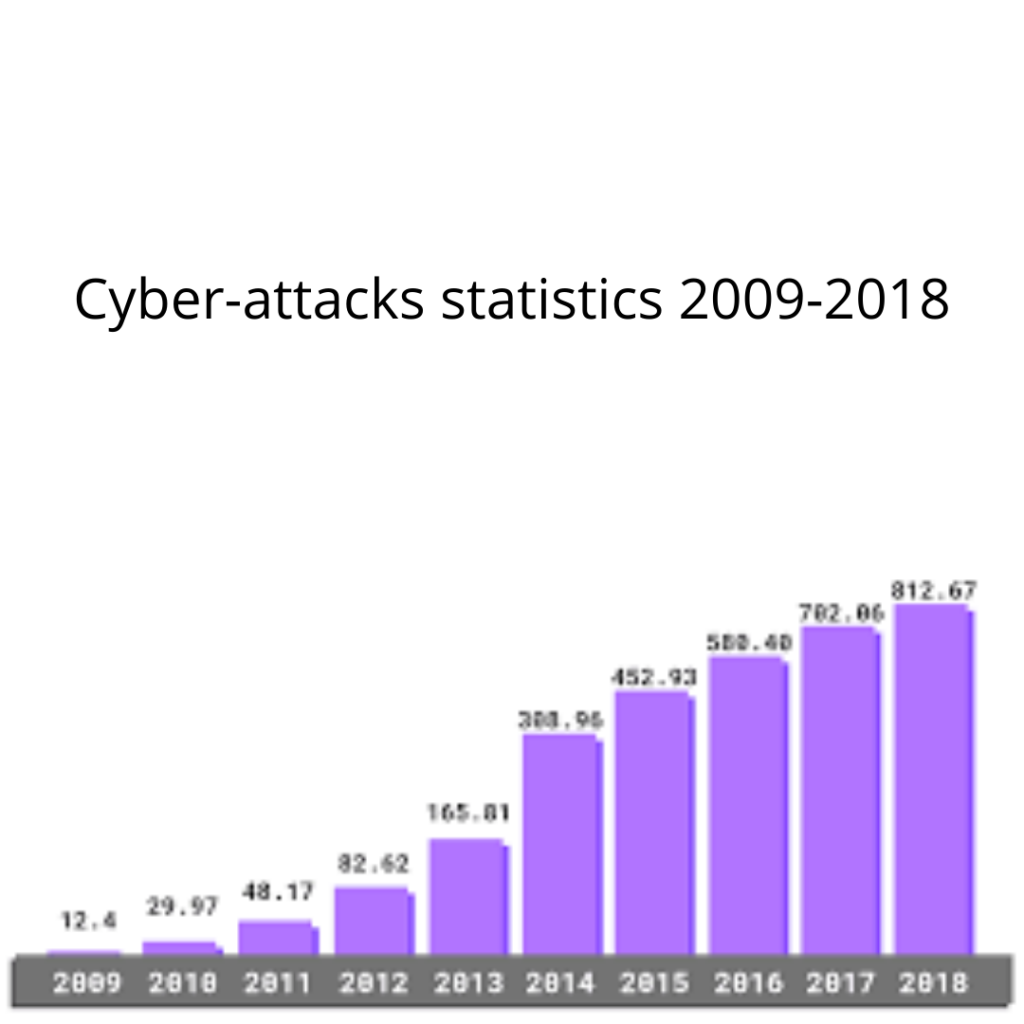
What can be done?
As cyber-attacks have become more common and frequent in the virtual world today, the only way to protect us from these attacks is to have a strict cybersecurity set up or a policy.
Advantages : We know that Cybersecurity threats are the problems of the day. Having a proper security system can help us overcome it to an extent. The advantages of having a Cybersecurity policy are
- A proper Cybersecurity system can protect your data
- It provides safer working conditions
- Your firm’s productivity level is maintained
- Keeps your website live
- It can act as a shield to protect your business from going down
- Restricts access to spyware, phishing mails and adware.
Cyber Security
Cybersecurity is not about creating an invulnerable system but, it is all about how to avoid or reduce the risk of the systems being confidential, availability and integrity without authorization. Cybersecurity, computer security, or Information technology security is the process of protecting and recovering computer systems, devices, programs, and networks from cyber-attacks, or damages. These attacks are aimed at accessing, destroying, and changing confidential or sensitive information that is collected from small businesses, health care institutions, government agencies, finances and military; extracting money from users. Cybersecurity has layers of protection across the devices, network, data, or programs to keep safe. It is everyone’s responsibility (the people, technology, processes) to create effective protection against cyberattacks.

Why is Cyber Security OUR Responsibility?
Cyber-attacks can happen to anyone. It does not stop at an organizational level. It comes down to every individual who has access to the internet. The issue is that not all are aware of the factor. Moreover, even if you are aware of it, we take our data security for granted. In an organization, it is not only the top layer employees who can be held responsible for safeguarding the data. This is equally applicable to everyone. Studies have found that about 50% of employees in various organizations are not concerned about the importance of cybersecurity.
When under an attack, most of us would blame the IT team of a company in case of a cyber attack. However, there is a limit for a specific team to make the data impenetrable. It takes a joint effort from everyone to keep our data safe. Let it be an external mail that you receive on your official system or a random link that pops up while you are browsing.
We have seen the news about individuals losing money, sometimes to an extent of risking their lives due to cyber-attacks. Always be on your guard while you are online. A single link can overturn your life. Technology evolves at a very fast pace. However these technologies will not be sufficient to protect you. It is you who have to be vigilant.
What To Do
We should have a strong cybersecurity culture to help us tackle cybersecurity threats. People should understand and follow basic principles like choosing a strong password when creating Gmail, Facebook, or any other social media accounts to secure their information. Try changing your password credentials on a regular interval. Never share your online credentials with anyone. Keep your devices locked and log out of the sites when you are not using them. Be careful to use a secure connection while using the internet.
Follow Cybersecurity principles as they provide tactical guidance on how organizations can protect their data from cyberattacks. It explains how you can govern, protect, detect and respond to risks. Technology acts as the main component in providing individuals and organizations the necessary tools to equip themselves with cybersecurity.
At the Organizational level:
Have awareness drives or learn proper cybersecurity sessions on how to protect your data. Ensure you understand the consequences of these attacks. Also if you are using a corporate network set up, ensure that you are following the guidelines determined by the company. Manage user privileges if multiple people have access to the internet from a particular network. If any incident occurs, frame a proper and functional policy to overcome the issue. Malware can attack you anytime. So keep an eye out for the same. Never attach any device that cannot be trusted. Also, random emails from unknown sources have to be checked properly before you go forward. Maintain a proper anti-malware watch-out policy as well as regulation on the media content. Scan everything before you use them. Monitor your device and keep your network security up-to-date.
Conclusion
Cyber threats are exploding, organizations like small businesses, medical organizations etc., are at a great risk. Cyber-attacks can happen at any point of time to anyone. Be careful and always follow the mentioned steps to prevent it. It is important to follow the steps in safeguarding business technologies, information and processes to avoid these cyber threats. The technology will prevent it to an extent, but you have to be vigilant and adhere to be safe and secure. The most important thing is to be aware of the possible risks and act wisely.

